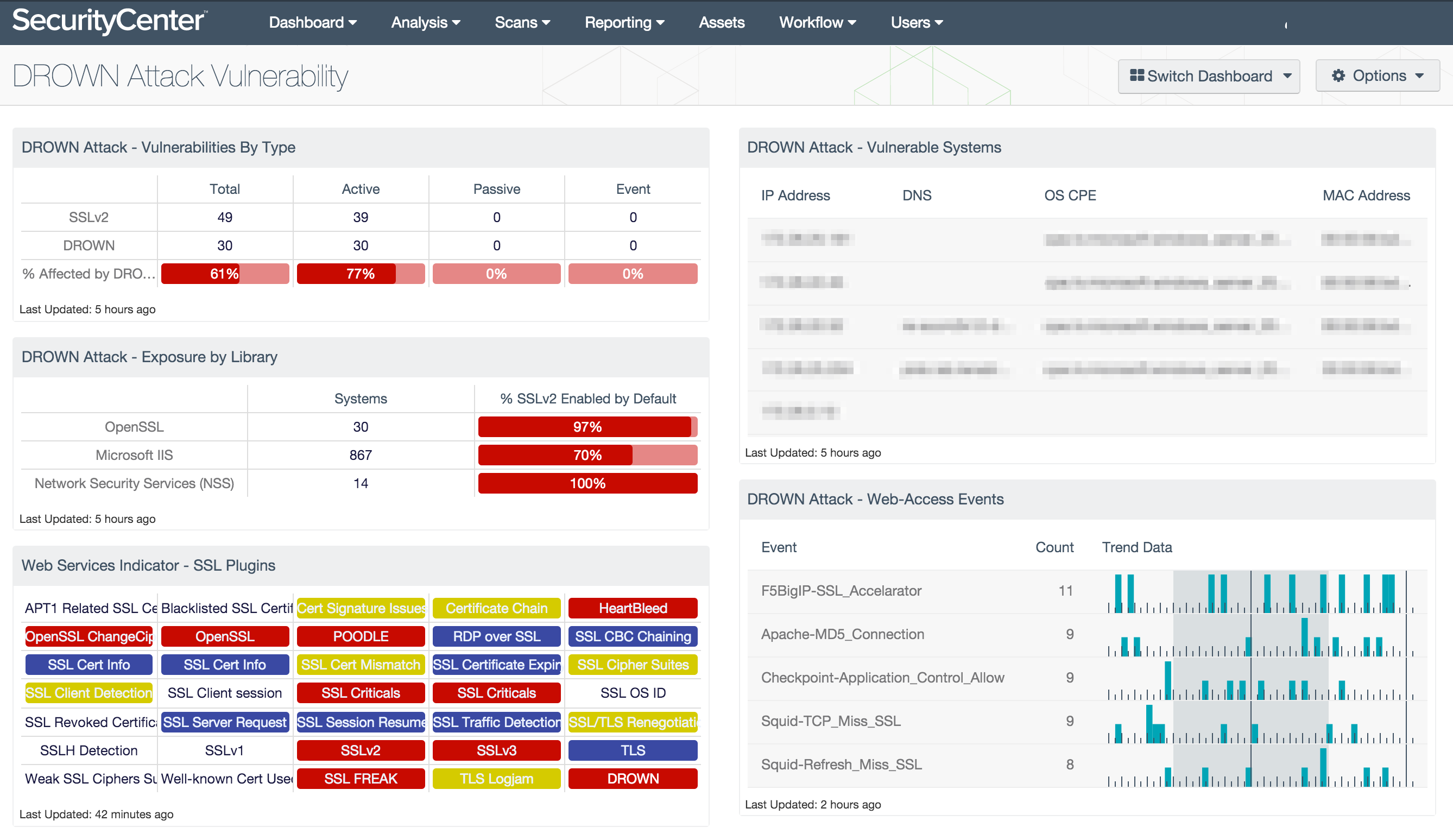
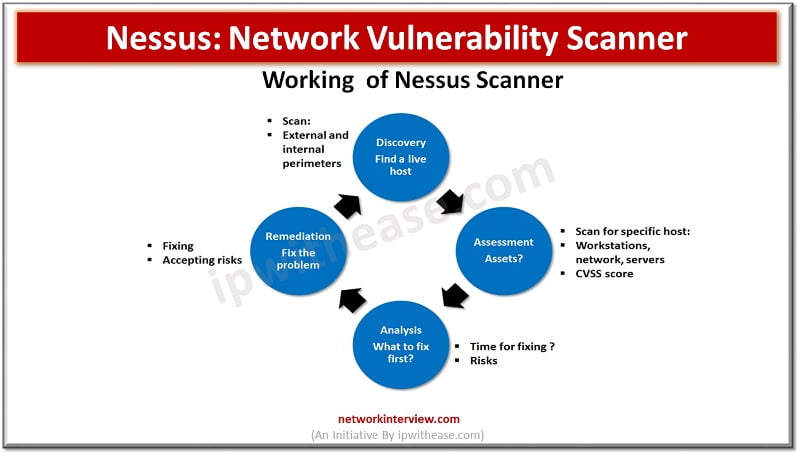
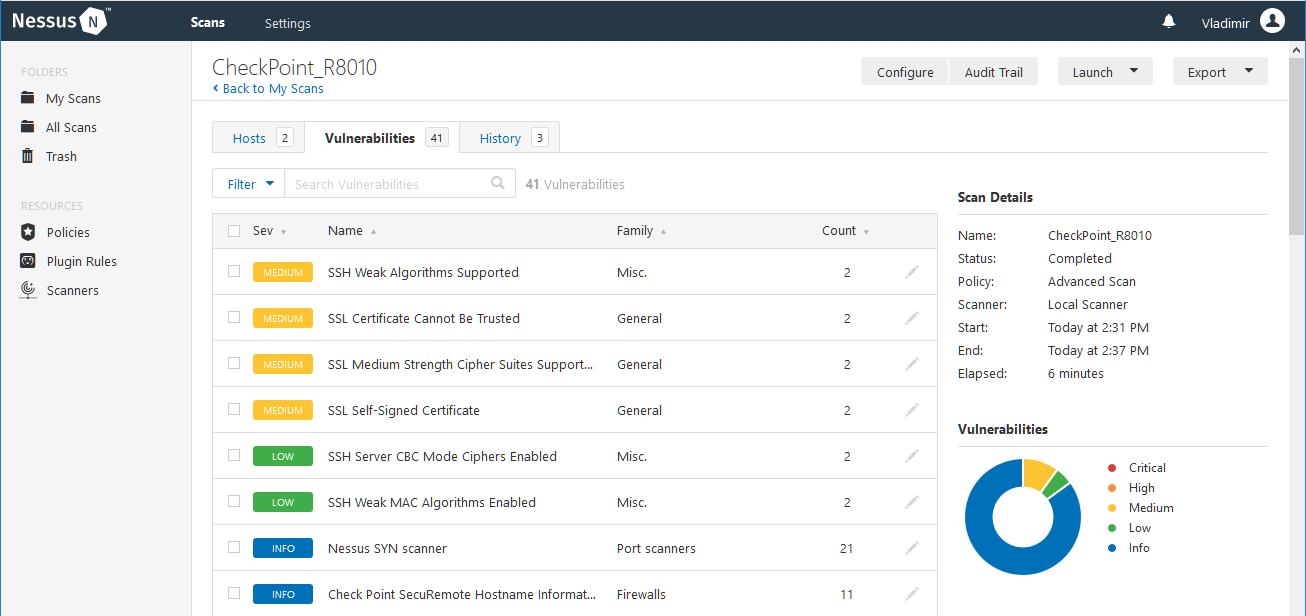
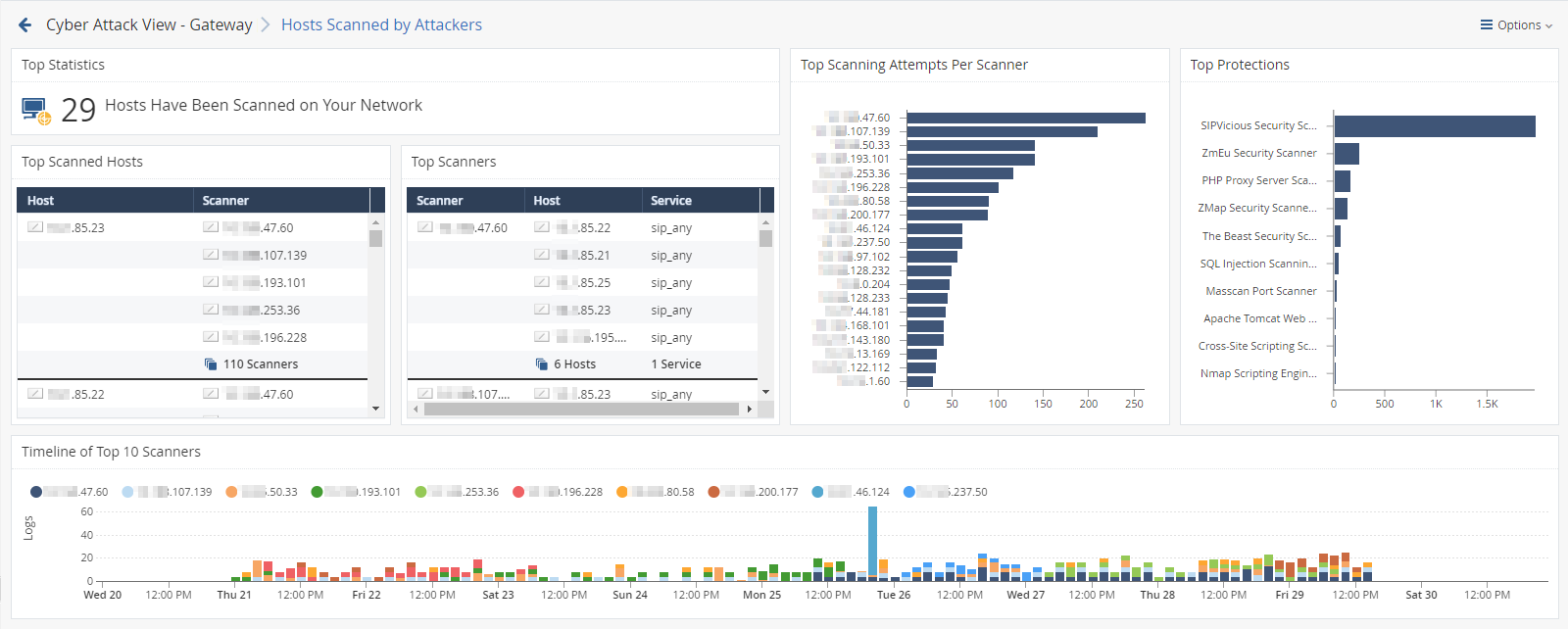
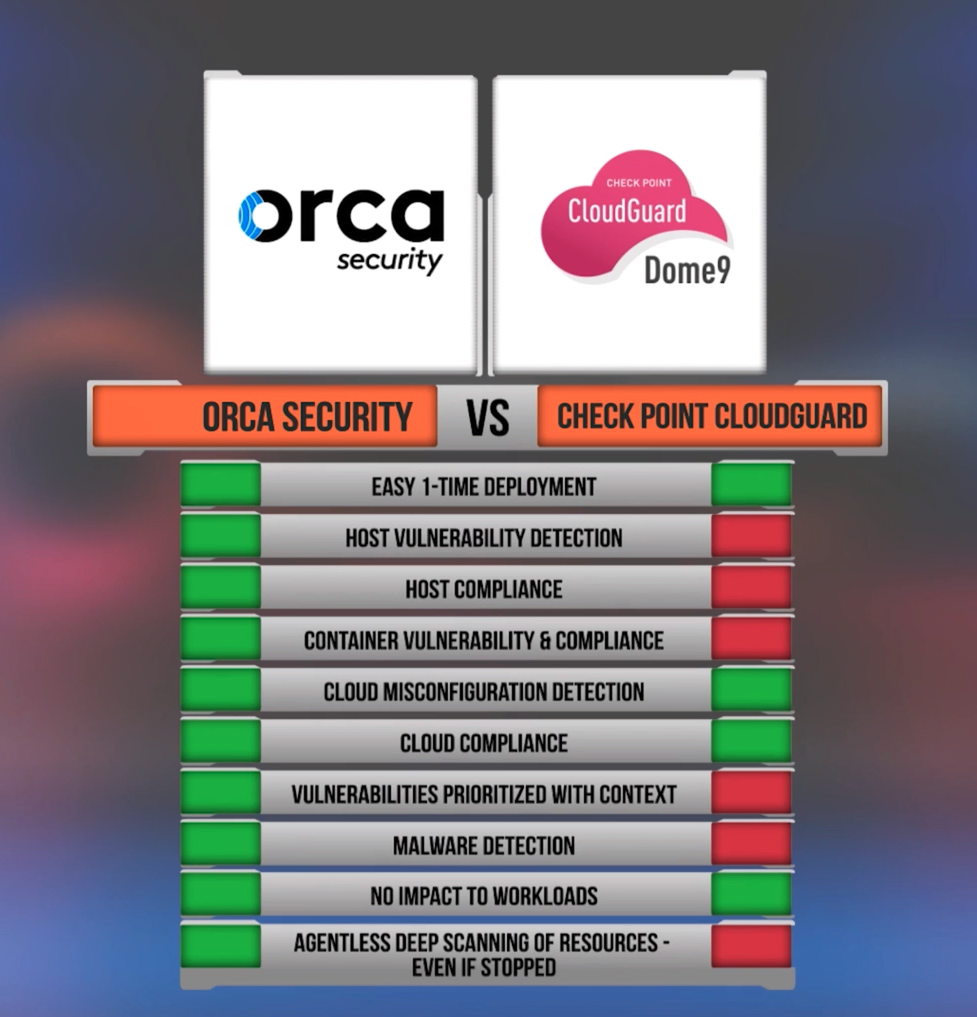
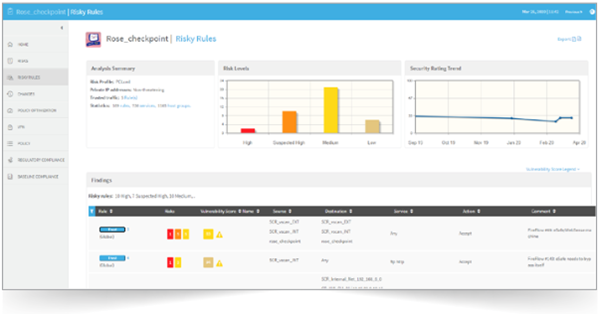
Check Point Software Technologies Bolsters Endpoint Security with Enhanced Posture Management to Tackle Escalating Vulnerability Exploits

Check Point Software Technologies Bolsters Endpoint Security with Enhanced Posture Management to Tackle Escalating Vulnerability Exploits - NCNONLINE



![Breaking News] SandBlast Agent Protects Against B... - Check Point CheckMates Breaking News] SandBlast Agent Protects Against B... - Check Point CheckMates](https://community.checkpoint.com/t5/image/serverpage/image-id/1374iAE731A99E43BC111/image-size/large?v=v2&px=999)